Paper accepted to TIST: Simplifying Data Disclosure Configurations in a Cloud Computing Environment
|
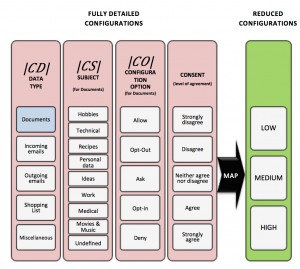
Rony’s paper, along with Oded Maimon and myself was just accepted to the ACM Transactions on Intelligent Systems and Technology (TIST)! The paper, titled “Simplifying Data Disclosure Configurations in a Cloud Computing Environment”, presents an algorithm for finding the optimal default privacy options. This image summarizes what we actually do: we take complex of privacy configurations (think Facebook sharing options), and reduce these options to a small set of feasible and representative options (like, 3 of them), that can be easily handled by the user. Here is the abstract: Cloud computing offers a compelling vision of computation, enabling an unprecedented level of data distribution and sharing. Beyond improving the computing infrastructure, cloud computing enables a higher level of interoperability between information systems, simplifying tasks such as sharing documents between co-workers or enabling collaboration between an organization and its suppliers. While these abilities may result in significant benefits to users and organizations, they also present privacy challenges due to unwanted exposure of sensitive information. As information sharing processes in cloud computing are complex and domain-specific, configuring these processes can be an overwhelming and burdensome task for users. This article investigates the feasibility of configuring sharing processes through a small and representative set of canonical configuration options. For this purpose, we present a generic method, named SCON-UP (Simplified CONfiguration of User Preferences). SCON-UP simplifies configuration interfaces by using a clustering algorithm that analyzes a massive set of sharing preferences and condenses them into a small number of discrete disclosure levels. Thus, the user is provided with a usable configuration model while guaranteeing adequate privacy control. We describe the algorithm and empirically evaluate our model using data collected in two user studies (n=121 and n=352). Our results show that on average 82% of the population can be covered by at least one option, when provided with three canonical configuration options. We exemplify the feasibility of discretizing sharing levels and discuss the tradeoff between coverage and simplicity in discrete configuration options. |