New published paper: Analyzing and Optimizing Access Control Choice Architectures in Online Social Networks
|
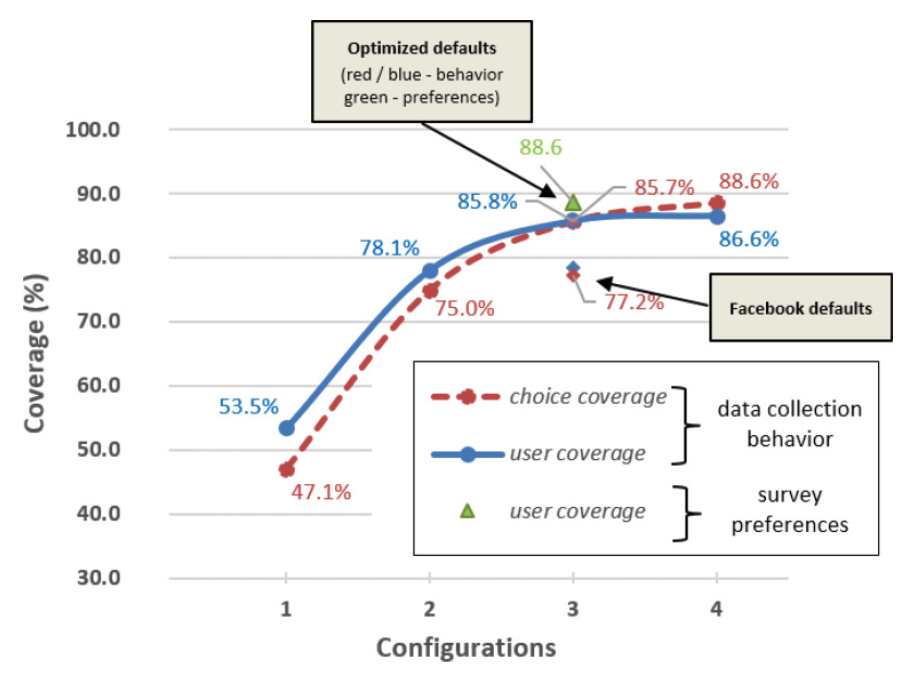
ACM Transactions on Intelligent Systems and Technology (TIST) had just published our paper, “Analyzing and Optimizing Access Control Choice Architectures in Online Social Networks“, with Rony Hirschprung, Hadas Schwartz-Chassidim, Tamir Mendel, and Oded Maimon. In a nutshell, we have developed a tool that evaluates how privacy user interfaces are suited to the actions and preferences of their users. We have used information from 266 Facebook users and over 500 surveyed users, and analyzed how the interface provided by Facebook served its users. We show that Facebook’s interface accommodated the decisions of about 77% of its users. It’s not too bad, but it can be improved to about 85% using our algorithm.
You can download the paper from the ACM page or download a final draft from here. Citation Ron Hirschprung, Eran Toch, Hadas Schwartz-Chassidim, Tamir Mendel, and Oded Maimon. 2017. Analyzing and Optimizing Access Control Choice Architectures in Online Social Networks. ACM Trans. Intell. Syst. Technol. 8, 4, Article 57 (May 2017), 22 pages. Abstract The way users manage access to their information and computers has a tremendous effect on the overall security and privacy of individuals and organizations. Usually, access management is conducted using a choice architecture, a behavioral economics concept that describes the way decisions are framed to users. Studies have consistently shown that the design of choice architectures, mainly the selection of default options, has a strong effect on the final decisions users make by nudging them toward certain behaviors. In this article, we propose a method for optimizing access control choice architectures in online social networks. We empirically evaluate the methodology on Facebook, the world’s largest online social network, by measuring how well the default options cover the existing user choices and preferences and toward which outcome the choice architecture nudges users. The evaluation includes two parts: (a) collecting access control decisions made by 266 users of Facebook for a period of 3 months; and (b) surveying 533 participants who were asked to express their preferences regarding default options. We demonstrate how optimal defaults can be algorithmically identified from users’ decisions and preferences, and we measure how existing defaults address users’ preferences compared with the optimal ones. We analyze how access control defaults can better serve existing users, and we discuss how our method can be used to establish a common measuring tool when examining the effects of default options.
|